NOTE: This has been updated on 15 June 2015 to include use of sha256 and sha256 startcom intermediate cross signing certificate. This will still give you an A+ rating.
Here is a quick configuration to use allowing A+ certification for your apache webserver.
NOTE: In order for ECDHE to work you MUST be using apache2.4 or greater(see here)
First goto your apache conf dir (/etc/apache2/)
create an ssl directory if it does not exist
mkdir ssl
cd ssl
cd ssl
If you have multiple vhosts it is a good idea to separate your certificates
mkdir vhostname
cd vhostname
cd vhostname
now generate your CSR we will use to request our certificate
openssl req -sha256 -out vhostname.csr -new -newkey rsa:4096 -nodes -keyout vhostname.key
This will generate a 4096bit RSA CSR we will use for the next step.Copy the content of the vhostname.csr
Goto the following website:
StartSSL
Goto the validation wizard and generate a domain validation for your domain
Once you have received your validation email and entered the key go back to the certificate wizard tab
Select "Web Server SSL/TLS Certificate"
Skip the generate private key section (we created ours just before)
Paste in the content from your vhostname.csr
Create your subdomain to generate and add a SAN (eg www.vhosthostname)
Once your key has been generated create a new file "vhostname.crt" in your vhostname directory
now download the StartSSL certificate as we need to add it later in our virtualhost
wget https://www.startssl.com/certs/class1/sha2/pem/sub.class1.server.sha2.ca.pem -O sub.class1.server.ca.pem
Secure your keys
chmod 400 *
goto your vhost configuration
(somewhere in /etc/apache2/sites-enabled/)
default is 000-default however I usually create one per site im hosting
Here is an extract:
<virtualhost *:80>
ServerAdmin webmaster@vhostname.com
ServerName www.vhostname.com
ServerAlias vhostname.com
Redirect permanent / https://www.vhostname.com
</VirtualHost>
<virtualhost *:443>
ServerAdmin webmaster@vhostname.com
ServerName www.vhostname.com
Header always set Strict-Transport-Security "max-age=163072000; includeSubDomains"
DocumentRoot /var/www/vhostname
<directory />
Options FollowSymLinks
AllowOverride None
</Directory>
<directory /var/www/vhostname>
Options Indexes FollowSymLinks MultiViews
AllowOverride None
Order allow,deny
allow from all
</Directory>
ScriptAlias /cgi-bin/ /usr/lib/cgi-bin/
<directory "/usr/lib/cgi-bin">
AllowOverride None
Options +ExecCGI -MultiViews +SymLinksIfOwnerMatch
Order allow,deny
Allow from all
</Directory>
ErrorLog ${APACHE_LOG_DIR}/error_vhostname.log
# Possible values include: debug, info, notice, warn, error, crit,
# alert, emerg.
LogLevel warn
CustomLog ${APACHE_LOG_DIR}/access_vhostname.log combined
SSLEngine on
SSLProtocol all -SSLv2 -SSLv3
SSLHonorCipherOrder on
SSLCipherSuite ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4
SetEnvIf User-Agent ".*MSIE.*" nokeepalive ssl-unclean-shutdown
SSLCertificateFile /etc/apache2/ssl/vhostname/www.vhostname.com.crt
SSLCertificateKeyFile /etc/apache2/ssl/vhostname/www.vhostname.com.key
SSLCertificateChainFile /etc/apache2/ssl/vhostname/sub.class1.server.ca.pem
</VirtualHost>
SSLUseStapling on
SSLStaplingResponderTimeout 5
SSLStaplingReturnResponderErrors off
SSLCACertificateFile /etc/apache2/ssl/vhostname/sub.class1.server.ca.pem
SSLStaplingCache shmcb:/var/run/ocsp(128000)
ServerAdmin webmaster@vhostname.com
ServerName www.vhostname.com
ServerAlias vhostname.com
Redirect permanent / https://www.vhostname.com
</VirtualHost>
<virtualhost *:443>
ServerAdmin webmaster@vhostname.com
ServerName www.vhostname.com
Header always set Strict-Transport-Security "max-age=163072000; includeSubDomains"
DocumentRoot /var/www/vhostname
<directory />
Options FollowSymLinks
AllowOverride None
</Directory>
<directory /var/www/vhostname>
Options Indexes FollowSymLinks MultiViews
AllowOverride None
Order allow,deny
allow from all
</Directory>
ScriptAlias /cgi-bin/ /usr/lib/cgi-bin/
<directory "/usr/lib/cgi-bin">
AllowOverride None
Options +ExecCGI -MultiViews +SymLinksIfOwnerMatch
Order allow,deny
Allow from all
</Directory>
ErrorLog ${APACHE_LOG_DIR}/error_vhostname.log
# Possible values include: debug, info, notice, warn, error, crit,
# alert, emerg.
LogLevel warn
CustomLog ${APACHE_LOG_DIR}/access_vhostname.log combined
SSLEngine on
SSLProtocol all -SSLv2 -SSLv3
SSLHonorCipherOrder on
SSLCipherSuite ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4
SetEnvIf User-Agent ".*MSIE.*" nokeepalive ssl-unclean-shutdown
SSLCertificateFile /etc/apache2/ssl/vhostname/www.vhostname.com.crt
SSLCertificateKeyFile /etc/apache2/ssl/vhostname/www.vhostname.com.key
SSLCertificateChainFile /etc/apache2/ssl/vhostname/sub.class1.server.ca.pem
</VirtualHost>
SSLUseStapling on
SSLStaplingResponderTimeout 5
SSLStaplingReturnResponderErrors off
SSLCACertificateFile /etc/apache2/ssl/vhostname/sub.class1.server.ca.pem
SSLStaplingCache shmcb:/var/run/ocsp(128000)
We can see here we have a perm redirect from the HTTP site to the HTTPS site.
Header always set Strict-Transport-Security "max-age=63072000; includeSubDomains" will force the browser from now on to connect ONLY via HTTPS
We turn on the SSLEngine
We disable SSLv2 and v3(not secure)
We force the ciphers to be honored in the order listed(eg to use the strongest possible
We set the CipherSuite (This method only allows AES-265 which can disable java from working. In this case use the following:
SSLCipherSuite ECDHE-RSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4
The SetEnvIf protects server side against an attack known as BEASTWe then set our certificates
Outside of the VirtualHost tag we set OCSP stapling which stops the clients going to check OSCP every request(speeds up processing keeping it server side).
Now restart apache (service apache2 restart) and you should be good to go. Check out your score on https://www.ssllabs.com
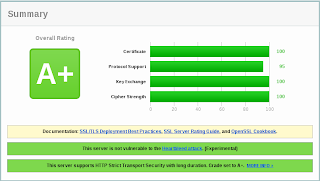
Let me know how you get on down below in the comments. Obviously I have written this very "quickly" and it requires some knowledge of linux and openssl. Using this configuration gives me the following: